TL;DR: Earlier this summer the SCA configured their Neon CRM membership portal to show registered users their member number. I discovered a vulnerability in Neon One’s software that allowed technically-savvy users to use that capability to change their member number to any value they desired.
After this was reported, the link to the vulnerable screen was removed, but the screen still exists and the vulnerability in the underlying Neon CRM software appears to remain unpatched.
In February the SCA completed the migration of its membership data from an aging legacy system (“Members Only”) to a new platform hosted by Neon One. Their Neon CRM service now appears to function as the system of record for the Society’s member records, including modern names, addresses, and payment information, as well as SCA-specific data such as Society name, kingdom, and member number.
In addition to its use by Society officers, the Neon CRM system also includes “member portal” functionality that allows people to update their personal information, pay for memberships, and purchase items from the SCA marketplace. These services seem to work well, and are a welcome alternative to conducting all such interactions via postal mail, as had been the case decades ago.
But shortly after the new service launched, folks noted one awkward omission: there wasn’t anywhere in the portal interface where you could view your membership number.
While volunteers who hold officer positions might have memorized their member number (after having to include it on an endless stream of quarterly reports and other correspondence), most SCA members very reasonably only look this information up when they actually need it, and if their paper membership card wasn’t handy, it seems natural that they might turn to the membership portal.
The Neon CRM system didn’t natively expose this information because membership number (and kingdom) weren’t part of the core membership records that all organizations using their platform would track and display — instead, they are SCA-specific data, which Neon CRM stores as “custom fields.”
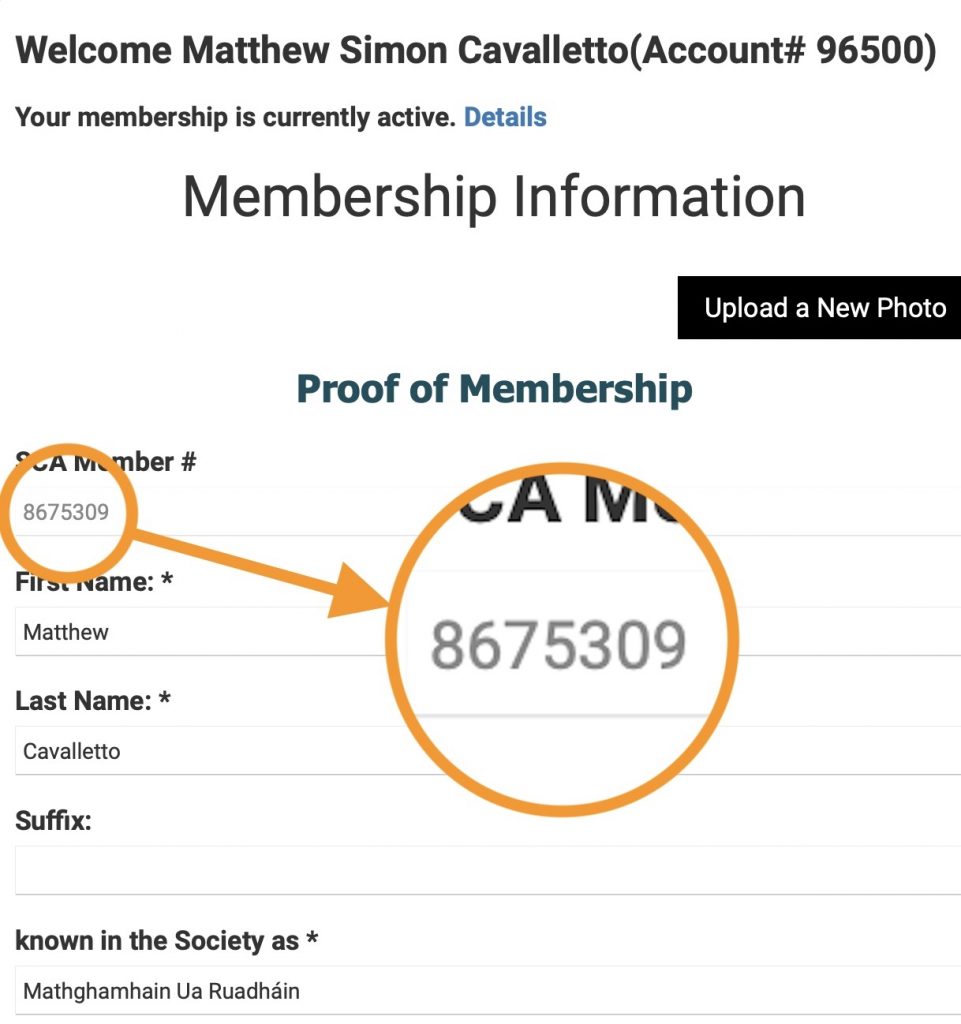
In May, the SCA configured their Neon CRM instance to add a “Membership Information” screen, which allowed people to edit their Society name, and to view (but not edit) their member number and kingdom.
In June, I discovered that technically-savvy users could use standard developer tools included in all modern web browsers to make those member number and kingdom fields editable, at which point a new member number and choice of kingdom could be entered and saved, with the results overwriting the supposedly-authoritative values.
To demonstrate the problem, I changed my membership number and kingdom in the Society’s database, and then changed them back. (I briefly considered leaving my membership number set to something amusing and having the Society mail me a new membership card to memorialize the issue, but managed to resist the temptation.)
To be clear, the vulnerability here was not caused by anyone in the SCA, nor is it specific to the Society — it appears to be a vulnerability in the underlying Neon CRM software, and likely affects any customers of that platform that use custom fields which end-users shouldn’t be able to alter.
Immediately after confirming the problem, I wrote to the Society IT Manager and the membership team to inform them of the issue. After some followup discussion, I agreed to postpone disclosure of the issue while they worked to validate and address the issue.
At some point in the following weeks, they took down the membership information screen which exhibited this vulnerability, and replaced it with a “Request A Proof of Membership Email” option that sends people the same information.
However, they never followed up with me, nor made any public announcement of the change, so after sixty days had passed without hearing from them, I sent a followup message and was told that the problem had been fixed.
Unfortunately, the fix that was made is only partial, and some aspects of the vulnerability remain, but given the limited impact of an exploit, perhaps that’s sufficient.
I’ve independently notified Neon One of this error.
Additional details are provided in the correspondence attached below.
[Update, August 31:] It appears that the vulnerability has not been fully remediated, so I’ve redacted additional portions of this email to reduce the exposure of sensitive information.
[Update, September 4:] I’ve re-sent my notification to Neon One, as the original email address their support representative gave me for this purpose bounced as undeliverable.
Please note this important warning: Although this blog post does include technical details, I have redacted several key elements needed to exploit it.
Furthermore, even if you figured out the mechanics, I would strongly counsel you against taking advantage of this vulnerability to change your membership number. There is a server-side audit trail that will allow these changes to be detected and reversed, and the SCA has previously sanctioned people for “hacking” member data — even when no hacking actually took place.
Date: June 26, 2023
From: Mathghamhain Ua Ruadháin
To: Society IT Manager
Cc: Society Membership Team
Hello,
I noticed that the membership information form now includes member number and kingdom.
[ Web address redacted for security reasons ]
I am writing to let you know that although these fields are marked disabled in the web user interface, they are not write-protected at the web application server.
As a result, a savvy user can very easily change their member number and kingdom, with these changes stored in the Neon CRM database.
I can provide further documentation of the mechanics of this if needed.
This appears to be standard behavior for Neon CRM custom fields that are marked as read-only, and is probably not something they can fix immediately, but it seems like it might be worth filing a ticket with them in hopes that they will eventually correct it.
I did not investigate to check whether this same mechanism would allow modification of other custom fields which are not exposed on this screen.
I’m not sure how to evaluate the severity of this issue; there is little to be gained by members in changing their membership number, aside from perhaps trying to impress friends with an implausibly low number suggesting very early membership in the Society, or getting a membership card issued with an amusing vanity number.
However, I suspect that such changes could wreak havoc on internal record-keeping, and could introduce problems in external systems that integrate this data such as kingdom-level warrant and authorization databases.
In the spirit of full disclosure: in order to confirm that this was an actual vulnerability, I briefly changed my membership number and kingdom, but then restored them to the prior, correct values. I believe these changes will show up in Neon CRM under Tools > Action Log, and you might be able to use that same capability to check whether any other accounts have had similar changes made via the end-user interface.
For the record, I did not gain privileged access to the Neon CRM back-end systems, I did not access anyone else’s member data, and I did not make any permanent changes to my own member data.
I would be interested in the Society’s evaluation of the severity of this issue and preferences regarding disclosure.
In service,
— Mathghamhain Ua Ruadháin
— Member number 231060… or at least that’s what the member portal currently says…
Date: June 26, 2023
From: Society IT Manager
To: Mathghamhain Ua Ruadháin
Cc: Society Membership Team
Hello,
Thank you for letting us know about this. We will investigate this with Neon and see if it is something that can be corrected. Please provide the mechanics of what you did so that we can share them with Neon.
I appreciate your efforts to ensure the IT security of the SCA. I will ask in the future that you not make any changes without bringing your suspicions to us first and coordinating with us. I feel like that is stepping over a rather significant line.
I agree that the significance of this is hard to judge. Until Neon has a chance to weigh in, I think it would be premature to make any determinations.
As to disclosure, until we can fully identify the risks associated with this issue and make appropriate corrections, public disclosure would do more harm than good.
Please use ‘helpdesk@sca.org’ when reporting technology related issues. Not only does it get everyone on ‘membership@sca.org’ it also gets to all the IT personnel.
Date: June 26, 2023
From: Mathghamhain Ua Ruadháin
To: Society IT Manager
Cc: Society Membership Team
To change your SCA membership number using Neon CRM:
- Navigate to members.sca.org
- Click “Membership Information”
- Make sure that your browser has “Developer Tools” enabled — the exact name varies depending on which browser you use.
- Open your browser’s “Web Inspector” tool in “Element Inspector” (aka DOM tree) mode.
- Click in the element list and use command-F to search for your personal membership number.
- Double-click on the attribute name to edit the
disabled="disabled"attribute, then remove both the name and the value. - Return your focus to the regular browser view of the membership form.
- Click on the now-editable “SCA Member #” field and type in a new value.
- Press return to submit the form.
The new value is saved and reappears when you refresh the membership form.
This process can also be used to edit other custom fields that are displayed in read-only mode on this form; I did not test whether it can be used to edit custom fields which are not included.
As mentioned earlier, I tested this process with my membership ID and kingdom and then reset them to their original values and contacted you.
I did not change any other data, I did not test this with any other member account, and I didn’t use any techniques other than what’s outlined above.
— Mathghamhain
Date: June 27, 2023
From: Mathghamhain Ua Ruadháin
To: Society IT Manager
Cc: Society Membership Team
On Jun 26, 2023, Society IT Manager wrote:
I appreciate your efforts to ensure the IT security of the SCA.
Thanks — I know it can be stressful to have these kinds of things pop up, but I think it’s better to know about them then to have them silently lurking undetected below the surface.
As to disclosure, until we can fully identify the risks associated with this issue and make appropriate corrections, public disclosure would do more harm than good.
Understood and agreed — I will hold off on publicly disclosing the details of this vulnerability so that folks have a chance to investigate and remediate.
In the spirit of full transparency, please be aware that this vulnerability isn’t a total secret, as I discovered it in the middle of a discussion on the Slack instance run by the Society Webminister (in fact, I was prompted to investigate it by an off-hand comment from one of the other webministers there) so some other folks in that group are also aware of the fact that these fields can be made editable — but that Slack is only accessible to a small number of senior folks in the webministry (and yourself) and they are all deeply invested in the Society’s success and don’t want to damage it… they’re more like co-workers than members of the public at large.
Please use ‘helpdesk@sca.org’ when reporting technology related issues. Not only does it get everyone on ‘membership@sca.org’ it also gets to all the IT personnel.
Sure thing — I thought that was specifically for issues with the main sca.org website, but now that I know who it reaches, I’m happy to use it for this other purpose as well.
In service,
— Mathghamhain
Date: August 24, 2023
From: Mathghamhain Ua Ruadháin
To: Society IT Manager
Cc: Society Membership Team
Hello,
Sixty days have passed since I made this report, so I figured I’d check in and see how things are going.
Have you had a chance to confirm the vulnerability, or assess its impact, or consider mitigations?
In service,
— Mathghamhain
Date: August 29, 2023
From: Society VP for Corporate Operations
To: Mathghamhain Ua Ruadháin, Society IT Manager
Cc: Society Membership Team
Thank you for your concern! This page was removed some time ago.
Date: August 29, 2023
From: Mathghamhain Ua Ruadháin
To: Society VP for Corporate Operations
Cc: Society IT Manager, Society Membership Team
Okay… I take this to mean that:
- This problem was confirmed to exist, and Neon One was not able to fix it in a timely manner.
- People wanting to confirm their membership number should now use the “Proof of Membership Email” feature, as the membership number is no longer visible on any page within the member portal.
- It’s okay for me to speak publicly about this issue.
Please let me know if I’ve misinterpreted any of the above!
Thanks,
— Mathghamhain
Date: August 29, 2023
From: Mathghamhain Ua Ruadháin
To: Society IT Manager
Cc: Society Help Desk
Hello again,
I wanted to send you one more follow-up on this issue.
[ Description of another possible vulnerability redacted for security reasons ]
Normally I would test this to confirm this is a real vulnerability before passing it along to you, but I have held back from testing it because of your previous guidance (“I will ask in the future that you not make any changes without bringing your suspicions to us first”).
I’d be happy to test it, if you’d like, and then to revert my changes back to their original values.
Even if it is confirmed, I think this vulnerability is less severe than the first version I reported, as it requires people to [ details of possible vulnerability redacted for security reasons ].
However, I’d still be inclined to pass it along to Neon, as we really don’t want to allow members to randomly mangle these values without supervision.
In service,
— Mathghamhain
Date: August 31, 2023
From: Mathghamhain Ua Ruadháin
To: Society VP for Corporate Operations
Cc: Society Help Desk
On Aug 29, 2023, Society VP for Corporate Operations wrote:
This page was removed some time ago.
For what it’s worth, although you’re no longer linking to it from the sidebar, the page I notified you about back in June does still exist, and likely still exhibits the same vulnerability.
[ Web address redacted for security reasons ]
That’s a fairly obscure web address, and you’re probably right in assuming that very few people would have bookmarked it, so it’s probably true that the chances of it being exploited are low.
I will remove that link from my blog post about this incident in order to avoid exacerbating the problem.
— Mathghamhain